I create my own checklist for the first but very important step: Enumeration.
Resources
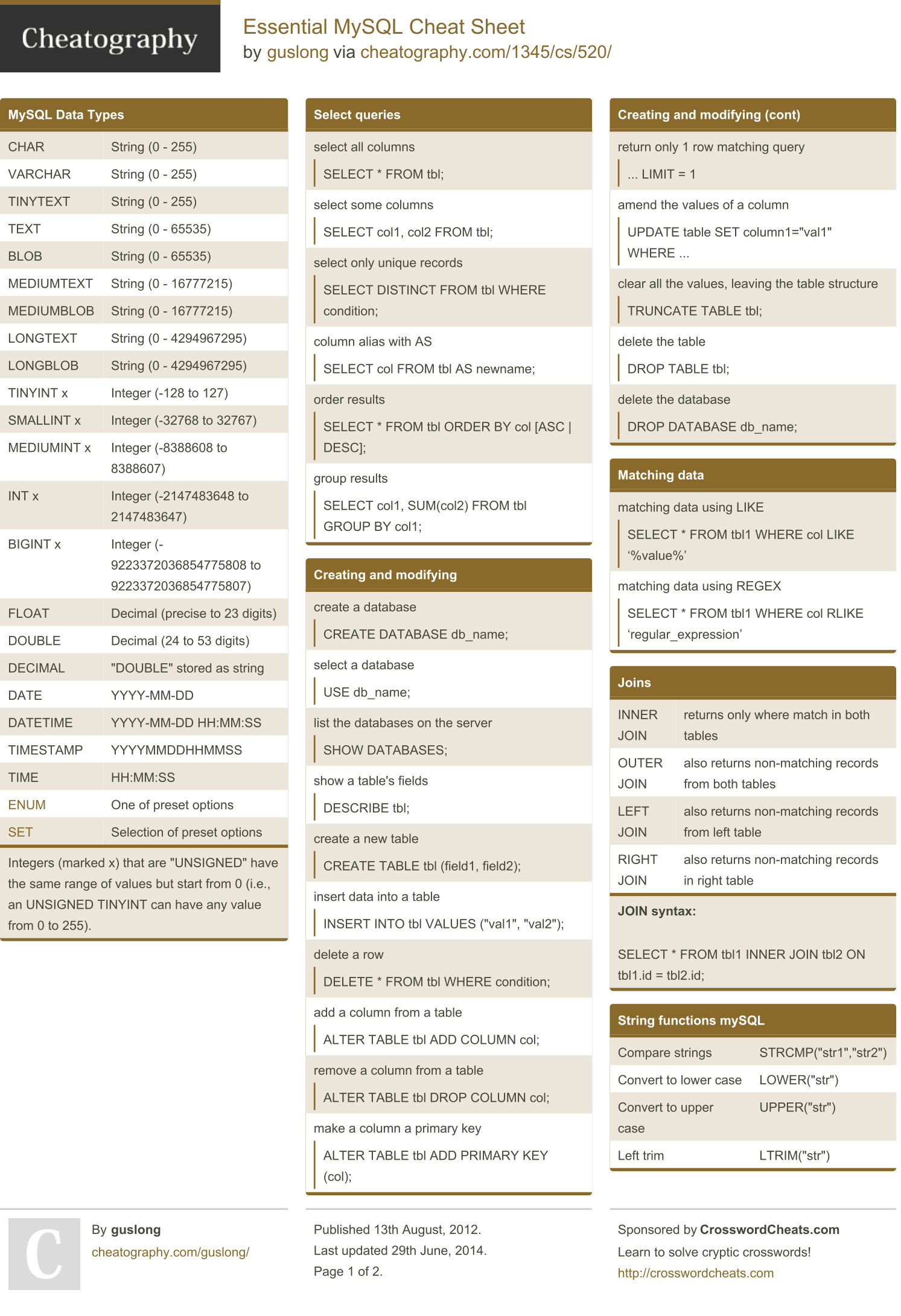
$ mysql # on another terminal mysql UPDATE mysql.user SET password=PASSWORD('newpass') WHERE user='root'; ## Switch back to the mysqldsafe terminal and kill the process using Control + $ /etc/init.d/mysql start Your commands may vary depending on your OS. 0 Comments for this cheatsheet. GitHub - kleiton0x00/Advanced-SQL-Injection-Cheatsheet: A cheat sheet that contains advanced queries for SQL Injection of all types. Github: K8s in 30 mins 🌟 This is not a comprehensive guide to learn Kubernetes from scratch, rather this is just a small guide/cheat sheet to quickly setup and run applications with Kubernetes and deploy a very simple application on single workload VM. This repo can be served as quick learning manual to understand Kubernetes. WebsiteSetuporg - MySQL Cheat Sheet. Numeric Data Types Unless programmed, the MySQL column display width will not limit the range of values that you can store there. Also, without a numeric data type integer, your columns can display width incorrectly if you include too wide values. To prevent that you can use the following integers to.
- Useful exploits: https://github.com/jivoi/pentest
Port 80/443/8000/8080 - HTTP
Web page
Open the web page, check http/https, check certificates to get users/emails
Click the plugin Wappalyzer to check web service & programming languages
Check
robots.txtto get hidden folders:curl -i $IP/robots.txtRun
nikto -h $IP -p $PORTClick all the links on the web page & always view page sources (
Ctrl + u), focusing onhref, comments or keywords likepassword,login,upload…If directory
Allow: PUT, try to upload text file then reverse shell through itGet folders/files
Download suspicious images & check:
exiftool $IMG,strings $IMG,xxd $IMG,steghide,binwalk $IMGFor open-source services, could download the codes and browse files to have better understanding on their functionalities, parameters, …
Searchsploitfor every service, software versionCheck path traversal on Linux and on Windows
Login forms
Check common creds:
admin/admin,admin/password,root/root,administrator/?,guest/guest…Search default creds of the web service on Google, documentations or usages (default users:
admin,root,root@localhost…)Capture
http-post-formusing BurpSuiteBrute-force with wfuzz using SecLists’s passwords (tut)
SQL injection
- First try
',1' or '1'='1-- -,' or '1'='1-- -,' or 1=1-- -
Tutorials
Cheat sheet: http://pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet
http://www.thegreycorner.com/2017/01/exploiting-difficult-sql-injection.html
Blind SQL injection
- HTB-Falafel: write Python script to brute force admin’s password
HTB-Charon: change
UNIONtoUNIoNto bypass the filter, bash script to enumerate a large number of rows in a table to get interesting credsMariaDB
- HHC2016 - Analytics: play with Burp Sequencer to capture the Cookies
- Oracle SQL
- Tutorial: http://www.securityidiots.com/Web-Pentest/SQL-Injection/Union-based-Oracle-Injection.html
- https://www.doyler.net/security-not-included/oracle-command-execution-sys-shell
- Cheat sheet: http://pentestmonkey.net/cheat-sheet/sql-injection/oracle-sql-injection-cheat-sheet
- MSSQL (Stacked Query)
https://www.exploit-db.com/papers/12975
https://perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/?_ga=2.122859595.1915973150.1589228589-1090418158.1589228589
http://pentestmonkey.net/cheat-sheet/sql-injection/mssql-sql-injection-cheat-sheet
https://webcache.googleusercontent.com/search?q=cache:KtfxjonYw58J:https://perspectiverisk.com/mssql-practical-injection-cheat-sheet/+&cd=1&hl=en&ct=clnk&gl=frhttp://www.securityidiots.com/Web-Pentest/SQL-Injection/MSSQL/MSSQL-Error-Based-Injection.html
https://gracefulsecurity.com/sql-injection-cheat-sheet-mssql/
Using
xp_cmdshell:- https://github.com/xMilkPowderx/OSCP/blob/master/SQLi.md, https://github.com/garyhooks/oscp/blob/master/REFERENCE/mssql.md
- HTB-Fighter
Bypass filters: https://portswigger.net/support/sql-injection-bypassing-common-filters
sqhs
- MySQL
- Cheat sheet, https://gracefulsecurity.com/sql-injection-cheat-sheet-mysql/
- VH-DC 9: tut
SQL Out-of-band exploitation
- (https://gracefulsecurity.com/sql-injection-out-of-band-exploitation/)
- HTB-Giddy
NoSQL
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection
- HTB-Mango
LFI/RFI
Use Nikto, which will sometimes return LFI/RFI Endnote v7.
Use Nmap’s HTTP NSE scripts
Check version names of the known CMS with know vulnerabilities, then simply Googling the version or whatever identifiable information
Bruteforce for directories and files, if PHPINFO() is present, check for allow_url and other indicators
If all else fails, fuzz parameter passings. Try to understand what the application is doing, many times it’s obvious that the parameter is looking for another file, like to a webpage; I.e: whatever.php?=home // this is looking to grab “home” which is likely a file stored locally. Try removing the value home, see how the server reacts. Try to read local files you know should exist on the file, depending on the OS maybe /etc/passwd for Linux and boot.ini for Windows. Use PHP wrappers such as php://filter/convert.base64-encode/resource=index to try to read the actual file whatever.php’s source code. This will convert it to base64 to prevent execution via the webserver. Decode it and you get the source code. Watch verbose error messages
Tutorials
- https://0ff5ec.com/lfi-rfi/
- https://highon.coffee/blog/lfi-cheat-sheet/#how-to-get-a-shell-from-lfi
- https://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability/
- https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601
PHP
- phpLiteAdmin: VH-Zico2
- Simple PHP Blog (sphpblog): VH-PwnOS
Wordpress
Brute-force
http://$IP/wp-admin,http://$IP/wp-login.phpMetasploit
- brute-force:
msf > use auxiliary/scanner/http/wordpress_login_enum
- brute-force:
Check
http://$IP/wp-content/themes,http://$IP/wp-content/uploads- Possible attack vectors:
- After login, upload php reverse shell in
404.phpof a theme (wp-content/themes/twentynineteen/404.php) msf > use exploit/unix/webapp/wp_admin_shell_upload- Upload malicious plugins in zip
- After login, upload php reverse shell in
Check interesting files:
/var/www/wp-config.phpCheck plugins’ vulnerability
- WordPress Plugin User Role Editor (https://www.exploit-db.com/exploits/44595): THM-Jack
Writeups
- Upload shell: VH-Stapler, VH-Mr. Robot
- ReFlex Gallery plugin: VH-Web Developer 1
- Activity Monitor plugin: VH-DC06
Joomla
Joomla 3.7.0 SQLi: https://github.com/XiphosResearch/exploits/tree/master/Joomblah
Drupal
Check
/CHANGELOG.txtfor Drupal versionFind
endpoint_pathand Services EndpointAttack vectors:
- Drupal 7.x Module Services - Remote Code Execution
- Drupalgeddon2 (March 2018): exploit
- Drupalgeddon3 (April 2018): exploit
Tutorials
Writeups
- Drupal v7.54: HTB-Bastard
- VH-DC1
Apache Tomcat
- Try default creds in
/manager: (tomcat/s3cret) - Deploy reverse shell in WAR format
Writeups
WebDAV
Port 21 - FTP
nmap scripts in
/usr/share/nmap/scripts/searchsploitFTP versionMetasploit
- Check version:
msf> use auxiliary/scanner/ftp/ftp_version - Anonymous login:
msf> use auxiliary/scanner/ftp/anonymous - Brute-force:
msf> use auxiliary/scanner/ftp/ftp_login
- Check version:
Brute-force with hydra
Check whether we can upload a shell, if so how to trigger the shell
Examine configuration files:
ftpusers, ftp.conf, proftpd.conf
Tutorials
- https://hackercool.com/2017/07/hacking-ftp-telnet-and-ssh-metasploitable-tutorials/
Very Secure FTP Daemon (vsftpd)
Writeups
v2.3.4 exploit
- HTB-Lame, HTB-LaCasaDePapel
ProFTPd
Tutorials
- https://hackercool.com/2020/03/hacking-proftpd-on-port-2121-and-hacking-the-services-on-port-1524/
Port 22 - SSH
Banner grab:
telnet $IP 22Try weak creds & Brute-force (exploitable in case of a very old version)
Crack passwords with john
Examine configuration files:
ssh_config, sshd_config, authorized_keys, ssh_known_hosts, .shostsProxychains
RSA tool for ctf: useful for decoding passwords
SSH with id_rsa of a user
Tutorials
- https://community.turgensec.com/ssh-hacking-guide/
Port 23 - Telnet
- Examine configuration files:
/etc/inetd.conf, /etc/xinetd.d/telnet, /etc/xinetd.d/stelnet
Writeups
Port 25 - SMTP
Connect
nmap scripts
Run smtp-user-enum
User enumeration (RCPT TO and VRFY) using iSMTP
Metasploit
- Search valid users:
use auxiliary/scanner/smtp/smtp_enum
- Search valid users:
Tutorials
- https://hackercool.com/2017/06/smtp-enumeration-with-kali-linux-nmap-and-smtp-user-enum/
Writeups
Mysql Injection Cheat Sheet Github
- JAMES smtpd 2.3.2: HTB-SolidState
- Enumeration: HTB-Reel
- Postfix Shellshock: exploit
Port 135, 136, 137, 138, 139 - Network Basic Input/Output System (NetBIOS)
Tutorials
- https://www.hackingarticles.in/netbios-and-smb-penetration-testing-on-windows/
Port 445 - SBM
nmap scripts
Find directories/files using wordpress’s wordlist
Enumerate with enum4linux
Enumerate samba share drives with smbmap
Get files recursively from the shared folder
smbclient (http://www.madirish.net/59)
rpcclient
Mount shared folders
Metasploit
msf> use auxiliary/scanner/smb/smb2msf> use auxiliary/scanner/smb/smb_versionmsf> use auxiliary/scanner/smb/smb_enumsharesmsf> use auxiliary/scanner/smb/smb_enumusersmsf> use auxiliary/scanner/smb/smb_loginmsf> use exploit/windows/smb/smb_delivery- EternalBlue (MS17-010):
msf> use exploit/windows/smb/ms17_010_eternalblue msf > use auxiliary/admin/smb/samba_symlink_traversal- SambaCry CVE-2017-7494:
msf> use exploit/linux/samba/is_known_pipename
Tutorials
- https://medium.com/@arnavtripathy98/smb-enumeration-for-penetration-testing-e782a328bf1b
- https://hackercool.com/2016/07/smb-enumeration-with-kali-linux-enum4linuxacccheck-smbmap/
- https://www.hackingarticles.in/penetration-testing-in-smb-protocol-using-metasploit/
- https://www.hackingarticles.in/multiple-ways-to-connect-remote-pc-using-smb-port/
- https://www.hackingarticles.in/a-little-guide-to-smb-enumeration/
Writeups
- MS-08-067, MS-17-010: HTB-Legacy
Ports 512, 513, 514 - Rexec & Rlogin
Tutorials
- https://hackercool.com/2020/03/hacking-rexec-and-rlogin-services-on-ports-512-513-and-514/
Extra Resources
- https://resources.infosecinstitute.com/what-is-enumeration/
Mysql Cheat Sheet Github
Port 3306 - MySQL
Connect the database
Decode passwords
Running as root: raptor_udf2 exploit, Lord of the Root CTF
Mysql Cheat Sheet Github Cheat
Port 3389 - Remote Desktop Protocol (RDP)
